The easy availability of large-scale data and its value have enhanced the importance of the Internet of Things (IoT). In the enterprise system, the IoT is often seen in the Office Automation (OA) and Operational Technology (OT) areas. These deployment scenarios help automate device management, improve efficiencies, and reduce operational costs with an eye on superior customer experience.
In a complete IoT ecosystem, multiple applications /devices can be interconnected, and they communicate with each other to process data and transmit it over a network. With an increasing number of enterprises getting connected to the IoT, multiple endpoints are created.
IoT and Its Impact on Security
IoT systems and devices can create bigger security risks for enterprises. The gathering of large-scale data by the IoT sensors and devices from their environments and users is inevitable. Connectivity between virtual and physical environments does shorten the distance between systems but can also allow cyberthreats.
A complex environment with devices working in a single IoT environment enables dynamic interactions between its devices and creates a wider attack surface. A centralized architecture set-up where data gathered by each device and sensor is communicated to a base station. In an enterprise, the main database could be the very same one used by thousands of devices that gather a phenomenal amount of data thus enhancing the risk factor.
Therefore, it becomes imperative to maintain secure interconnections with up-to-date software, password hygiene, deploying tools to manage vulnerabilities etc.

SAP Security in the Integrated IoT Environment
As organizations aspire to stay efficient and cost-competitive in their existing SAP ERP systems, seamless data integration is the next step. Integration of IoT with SAP simplifies data transfer and helps drill down into granular insights. Now, this offers stakeholders opportunities to obtain details of behavior and patterns and help make decisions to support business learning, decision-making, and overall business performance.
SAP Security is user administration in SAP for all the modules governing user access to data and processes inside an SAP landscape. It leverages all tools and processes to extend the right amount of access a given user needs to perform his /her role precisely. The module designates this access via a role or a position as against a person and hence accommodates an easier flow of information while being secure.
With SAP Security a business can obtain:
- Data integrity
- Protection against fraud and exploitation
- Easy identification of unauthorized access.
- Continuous and automated audits
- Information on data leaks
- Centralized system of security monitoring.
Since SAP systems connect different functions and applications to help in smoother business operations, the environment can get complicated, making it difficult to develop proper cybersecurity measures.
An integrated SAP- IoT environment certainly demands continuous improvements in security features. Considering the damage an enterprise faces in the wake of a data security breach, you need a dependable partner with the experience to implement security measures in an integrated IoT – SAP environment. Gemini Consulting & Services has helped clients across the globe to deploy the SAP Security module to protect their systems. Contact us to understand more about how you can reliably secure your IoT integrated SAP environment.
Here are the steps that can be adopted by SAP security as a systematic means to thwart IoT security threats.
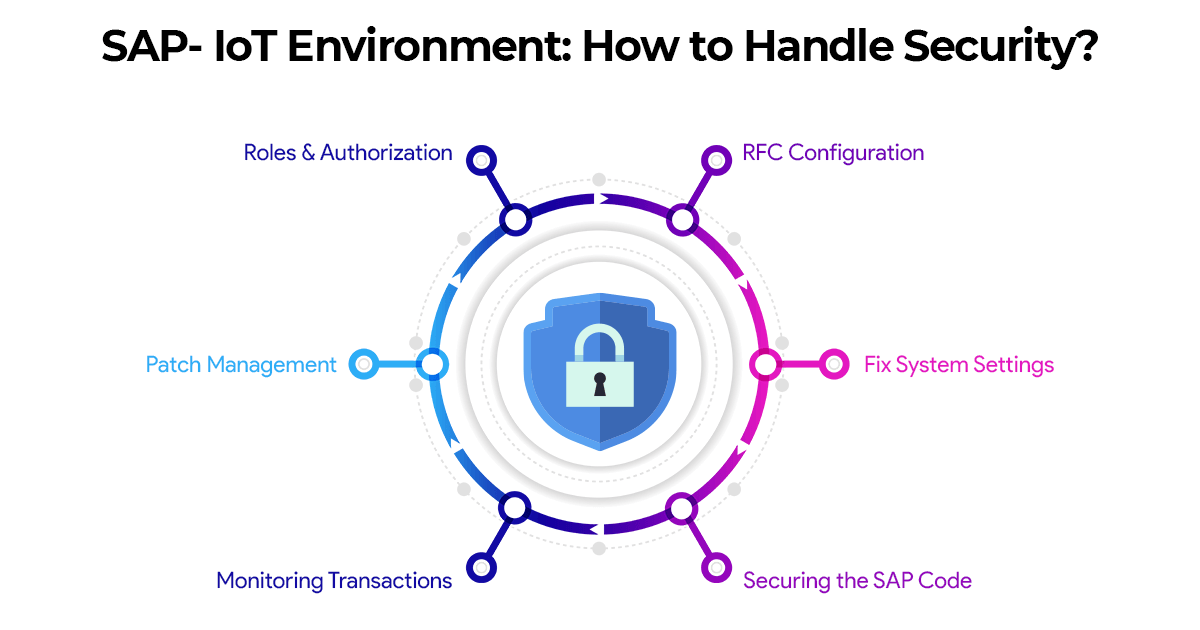
1. Roles and Authorization
In the SAP system, customer-specific authorization can be set up. This requires assigning essential permissions to users. The assignment of authorization combinations, such as Segregation of Duties (SOD) is important and can be used only in exceptional cases. Given that this can be easily manipulated; examining necessary authorizations and authorization combinations is crucial and can present businesses with challenges.
Now it becomes important to conduct continuous, automated reviews of SAP authorizations using a test catalog. Creating this from scratch is relevant for the authorizations in the SAP Basis area as well as in the business processes. Assuming 4-6 eye principles are undermined by a particular assignment of necessary permissions and combinations of permissions; there is a risk of exploitation or fraud. It is necessary therefore to accordingly understand the trigger of combination conflicts and allow further checks of other critical authorizations.
2. Patch Management
The way threats are handled in a traditional cybersecurity environment is also valid for SAP systems. Continuous publications of SAP Security Notes help organizations keep the SAP systems up to date for which continued application of such matches is necessary. Unpatched SAP systems end up with serious security gaps without knowledge of where the vulnerabilities are, and how they can be exploited.
3. Monitoring Remote and Physical Transactions
SAP offers a large number of critical transactions and functional modules that are even available remotely thereby helping create accounts via the SAP system’s API. Now, these can also be given authorizations and used accordingly leaving room for other function modules to simultaneously load or manipulate data from the SAP environment. It is hence a mandate to monitor the execution of transactions, RFC modules, or SAP reports continuously and in real-time. The same applies to access to SAP systems from outside via the interfaces of an SAP system as well.
4. Securing the SAP Code
Since in SAP systems, developers often ensure the ABAP code’s security, it gets carried out without sufficient examination of the coding. Coding is done in blocks and then transported. This leaves attackers a window for code injection as coding can be generated and executed at runtime. Luckily, SAP provides a code inspector, with modules like the Code Vulnerability Analyzer, to check the coding at all stages.
5. Fix Settings in the System
Settings are carried out at the database level by SAP transactions- SAP Profile Parameters, which are stored in files. The rollout of an SAP system must comply with a set of rules defined by the SAP Basis operating manual. Now, this determines security settings assigned in an SAP system, the extent of access and helps with communication within the system. The operating system, database, and application layers will require proper configuration of the security settings accordingly.
6. RFC Configuration and Read Access Logs
The RFC Gateway or the SAP-internal firewall needs to be configured precisely to avoid unauthorized remote access from systems and applications as per SAP best practice guidelines, or guidelines from SAP user groups. AP Security also covers a row of security logs-the most critical logs being the SAP Security Audit Log (SM20), which contains a set of security and audit-relevant conditions. Change Logs (SCU3) of database tables are available, along with changed user documents and business objects. The configuration of the SAP Read Access Logs and their evaluation is an essential element of SAP Security Monitoring, and this can help monitor access to an SAP system.