With increased attacks on enterprise systems, cybersecurity has become a major business priority. As we move into 2026, experts warn that cybercrime is becoming more intelligent, automated, and persistent. Powered by Artificial Intelligence (AI), modern cyberattacks are harder to detect, faster to launch, and capable of targeting organizations of any size.
In this blogpost, we explore the biggest cybersecurity risks expected in 2026 and outline practical strategies businesses can use to strengthen their defences and build long-term resilience.
Why Cybersecurity Is More Critical Than Ever
In a connected world, businesses rely heavily on cloud platforms, mobile devices, remote work tools, and third-party software. While these technologies improve productivity, they also expand the attack surface for cybercriminals.
Cyberattacks are no longer isolated incidents. They can lead to operational disruption, financial loss, legal consequences, and long-term damage to customer trust. As attacks grow more convincing and automated, organizations must move from reactive security to proactive, layered protection.
What Are Cybersecurity Threats?
Cybersecurity threats are malicious attempts to gain unauthorized access to systems, steal sensitive data, or disrupt business operations. These threats may come from external hackers, malicious insiders, or automated bots scanning the internet for vulnerabilities.
Common examples include phishing, ransomware, malware, credential theft, and denial-of-service attacks. In 2026, many of these threats will be enhanced by AI, making them more adaptive and difficult to stop.
Industry forecasts from Cybersecurity Ventures indicate that worldwide investment in cybersecurity tools and services is expected to surpass $520 billion per year by 2026, doubling from approximately $260 billion in 2021. In addition, a 2024–2025 McKinsey analysis suggests that the adoption of artificial intelligence is broadening the cybersecurity sector’s total addressable market to around $2 trillion.

1. AI-Driven Cyberattacks
Cybercriminals are increasingly using AI to automate attacks. These tools can scan systems for weaknesses, craft highly realistic phishing messages, and adapt in real time if blocked. Some attacks can now run continuously without human input, learning from failed attempts and improving over time.
2. Advanced Ransomware
Ransomware attacks are becoming smarter and more destructive. Instead of simply encrypting files, attackers now use “multi-extortion” tactics, stealing data, threatening leaks, and launching Distributed Denial of Service (DDoS) attacks simultaneously. AI helps attackers identify high-value targets and maximize pressure on victims.
3. Human Error and Social Engineering
Despite technological advances, people remain one of the weakest links in cybersecurity. Social engineering attacks, such as phishing, smishing (SMS phishing), scareware, and pretexting, exploit human trust rather than technical flaws. In 2026, AI-generated messages will closely mimic real colleagues, brands, and communication styles.
4. Deepfake Voice and Video Impersonation
AI can now convincingly clone voices and create fake video calls using publicly available recordings. Attackers use these deepfakes to impersonate executives or IT staff, tricking employees into approving payments or sharing credentials. Finance teams and system administrators are especially at risk.
5. Identity and Credential Theft
Weak passwords and poor identity management continue to enable breaches. AI-powered tools can test thousands of password combinations per second or use stolen credentials from the dark web to bypass security controls. Once inside, attackers can move through systems unnoticed.
6. Cloud Misconfigurations
Misconfigured cloud storage and overly broad user permissions remain a leading cause of data exposure. In 2026, attackers increasingly use automated tools to scan for these mistakes, meaning even a small oversight can quickly lead to a breach.
7. Supply Chain Attacks
Instead of attacking organizations directly, cybercriminals target trusted vendors, software providers, or SaaS platforms. A single compromised supplier can give attackers access to multiple businesses at once.
8. IoT and Operational Technology (OT) Vulnerabilities
Billions of connected devices, from smart sensors to medical and industrial systems, often lack strong security controls. These devices create new entry points that attackers can exploit if networks are not properly segmented.
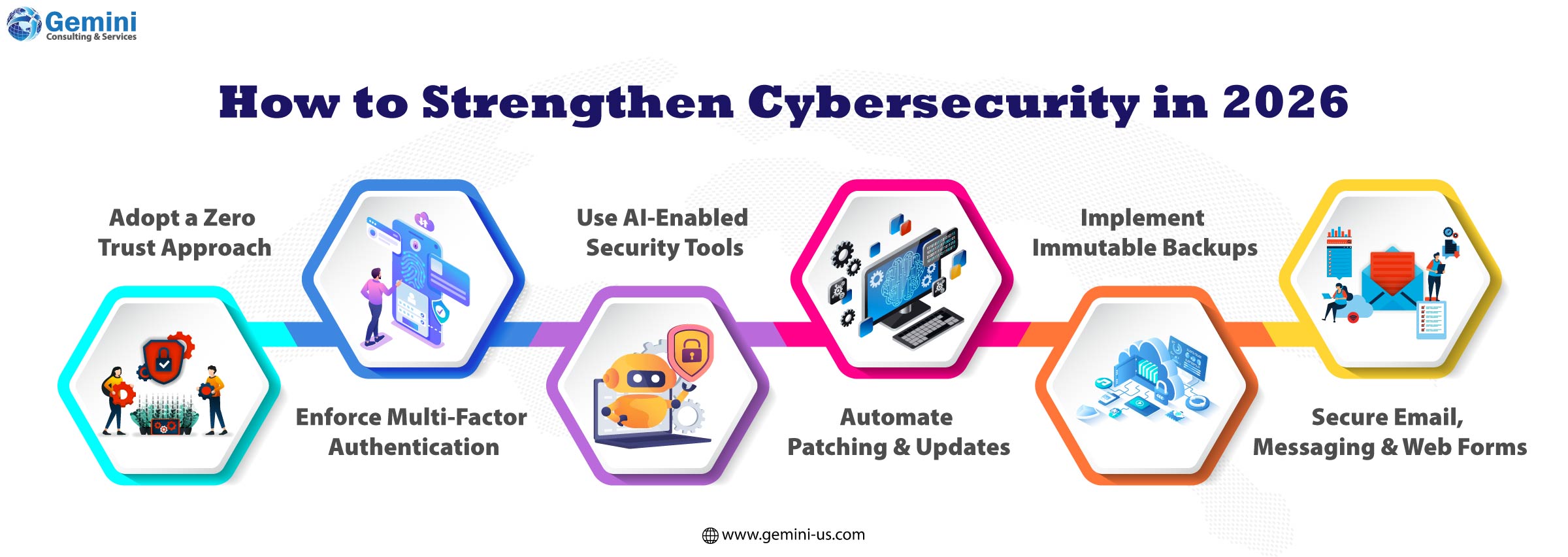
Adopt a Zero Trust Approach
Assume no user or device is automatically trusted. Verify every access request using strong authentication and continuous monitoring, regardless of location.
Enforce Multi-Factor Authentication (MFA)
MFA can protect enterprise systems and mitigate risks that are beyond passwords. It should be mandatory for email, cloud platforms, hosting accounts, administrative dashboards, and remote access tools.
Use AI-Enabled Security Tools
Just as attackers use AI, businesses must do the same. AI-driven cybersecurity platforms can detect unusual behavior, identify threats in real time, and automatically isolate suspicious activity before damage occurs.
Automate Patching and Updates
Attackers mainly target outdated software systems as they can gain easy access. Enable automatic updates for operating systems, applications, plugins, and cloud services, and remove unused software that increases risk.
Implement Immutable Backups
Backups should be protected from alteration or encryption by ransomware. Immutable backups ensure businesses can recover quickly without paying attackers.
Secure Email, Messaging, and Web Forms
Since phishing remains the most common attack method, advanced spam filtering is essential. Businesses should also protect contact forms and chat tools with CAPTCHA, input validation, and bot-detection techniques.
Strengthen Vendor and Supply Chain Security
Assess third-party providers carefully. Use vendor risk management programs, limit access privileges, and monitor integrations continuously.
Train Employees Continuously
Regular cybersecurity awareness training helps staff recognize phishing, fake support chats, deepfake calls, and other social engineering tactics. Simulated phishing tests can reinforce learning and reduce risk.
Develop and Test an Incident Response Plan
Every organization should have a clear plan outlining how to detect, contain, and recover from cyber incidents. Defined roles, communication steps, and recovery procedures reduce downtime and confusion during an attack.
What Industries to face most cyber threats?
Industries those have heavy reliance on AI, IoT, and cloud systems will be affected mostly in the coming years, such as manufacturing, telecom, and transportation, finance, healthcare, energy,
How Can Organizations Protect Against Top Cybersecurity Threats in 2026?
Implementation of zero-trust architectures, where no user or device is inherently trusted regardless of location, reduces the risk posed by negative credentials or devices.
Regular employee cybersecurity training remains vital, as human error is a consistent factor in many breaches. Awareness programs should highlight changing hacker tactics and reinforce safe online behaviour to mitigate hacking risks successfully.
At Gemini Consulting and Services, we help organizations reduce cybersecurity vulnerabilities and strengthen their defences. Our in-house cybersecurity experts deliver customized solutions for businesses of all sizes, ensuring they are prepared to withstand evolving cyber threats. Contact us to learn how Gemini can help your enterprise to reduce cybersecurity related risks.
Conclusion
In 2026, cyberattacks will be faster, smarter, and more convincing than ever before. Autonomous AI attacks, deepfake impersonation, cloud misconfigurations, and identity abuse will challenge traditional security approaches.
However, businesses that invest in layered defences, AI-powered security tools, strong identity management, and employee awareness can stay ahead of these threats. Cybersecurity is no longer optional, it is the foundation of trust, resilience, and long-term business success in the digital age.
By preparing today, organizations can face tomorrow’s cyber risks with confidence.



